Web Server Scanning With Nikto
Nikto is an open-source web server and web application scanner.
Nikto is an open-source web server and web application scanner designed to detect various security vulnerabilities. Developed by Sullo at CIRT, Inc., Nikto scans web servers for over 6700 potentially risky files/programs, checks for outdated server software, and identifies version-specific issues. Originally released in late 2001, it is currently maintained by David Lodge with contributions from other developers.
Key Features of Nikto:
- Detects SQL injection, XSS, and other common vulnerabilities.
- Identifies installed software via headers, favicons, and files.
- Guesses subdomains and supports SSL (HTTPS) websites.
- Generates reports in plain text, XML, HTML, or CSV formats.
- Explores web server content and reports unusual headers.
- Checks server configurations like multiple index files and HTTP server options.
- Supports HTTP proxy and can guess credentials for authorization.
- Customizable reports with a template engine and integrates with Metasploit.
How to Install Nikto
Nikto comes pre-installed on linux machines.
To test it out, simple run
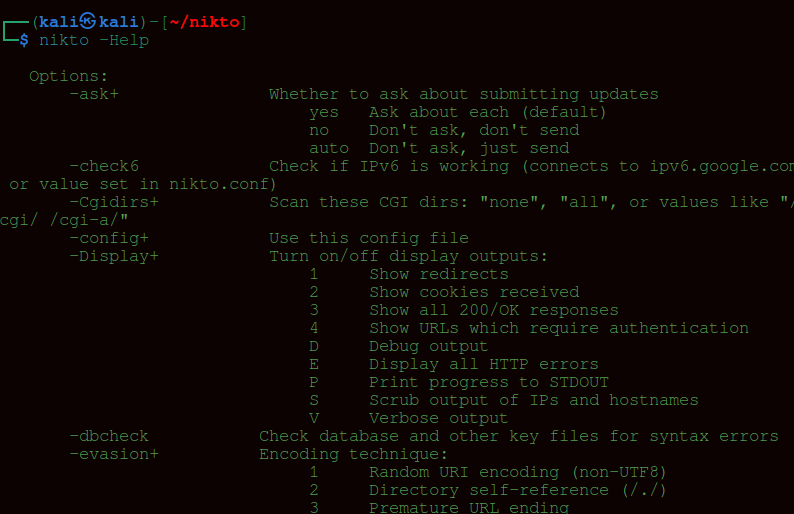
nikto -Help
Kali Linux: Nikto comes preinstalled under “Vulnerability Analysis.”
Other Linux distributions: Use
apt install niktoor obtain Nikto from GitHub.Windows: Install Perl from ActiveState, then download Nikto.
MacOS: Install using Homebrew.
How to Scan with Nikto
Now that you know what Nikto is and how to install it, let’s go ahead and run some scans. Since Nikto is a command-line tool, you can use the help command to get a list of options:
nikto -Help
How to Scan a Domain
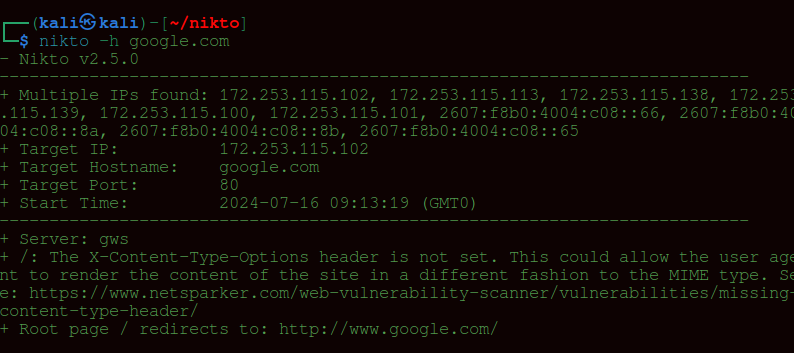
To perform a simple domain scan, use the -h (host) flag:
nikto -h google.com
How to Scan a Domain with SSL Enabled
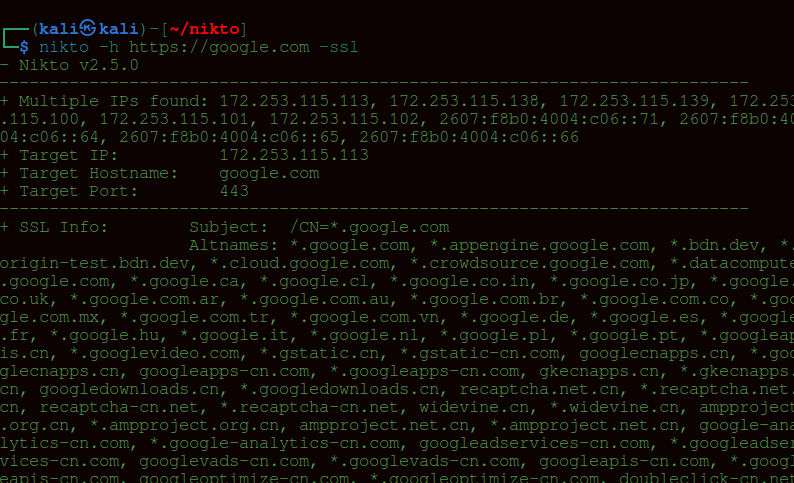
For domains with HTTPS enabled, you have to specify the -ssl flag to scan port 443:
nikto -h https://google.com -ssl
How to Scan an IP Address
Sometimes you just want to scan an IP address where a web server is hosted.
To do that, use the same -h flag you used for domain scanning:
nikto -h
How to Scan Multiple IP Addresses From a Text File
To scan multiple IP addresses or domains, just put them in a text file separated by newlines. Nikto will know that the scan has to be performed on each domain / IP address.
Let’s assume we have a file named domains.txt with two domain names:
google.com facebook.com
To scan both of them with Nikto, run the following command:
nikto -h domains.txt
How to Export Scan Results
Nikto scans take a while to complete. When you are a professional pen-tester, you don’t want to repeat scans very often unless there are major changes to the web application.
To export a scan result, use the -o flag followed by the file name:
nikto -h google.com -o scan.txt
You can also use the -Format flag to specify an output format. You can choose from CSV, HTML, nbe (Nessus format), SQL, txt, and XML:
nikto -h google.com -o scan.csv -Format csv
You also use Nikto with Metasploit
Nikto offers a way to export scans to Metasploit so that it gets easier when you try to exploit systems based on the scan results from Nikto.
To do that, append the -Format msf+ flag to the end of a scan:
nikto -h <domain/ip> -Format msf+
Conclusion
Nikto stands as a robust tool in the arsenal of web security professionals, offering comprehensive scanning capabilities to identify vulnerabilities in web servers and applications. With its extensive database of potential threats and its ability to generate detailed reports in multiple formats, Nikto empowers users to proactively safeguard their systems against a wide range of security risks. Continuously maintained and updated, Nikto remains a trusted choice for security assessments, providing essential insights that contribute to the resilience of web infrastructures worldwide.
Last updated 04 Sep 2024, 13:45 +0530 .