An Introduction to Metasploit
Learn more about the Metasploit framework.
Introduction to Metasploit
The Metasploit Framework is a robust and versatile tool used extensively in the field of cybersecurity. It serves a dual purpose, utilized by both ethical hackers and cybercriminals to identify and exploit vulnerabilities within networks and servers. As an open-source platform, Metasploit offers extensive customization and compatibility with various operating systems, making it a go-to resource for penetration testing and vulnerability assessment.
Understanding Metasploit
Metasploit allows penetration testers to deploy pre-written or custom scripts to explore network weaknesses. By simulating attacks, security professionals can uncover and document vulnerabilities, providing crucial information to address these issues and enhance system defenses. This proactive approach is a cornerstone of modern cybersecurity practices, ensuring that potential threats are identified and mitigated before they can be exploited maliciously.
Historical Background
The Metasploit Project was initiated in 2003 by H.D. Moore, originally as a Perl-based tool designed for network probing. With contributions from core developer Matt Miller, the project evolved and was fully rewritten in Ruby by 2007. In 2009, Rapid7, a Boston-based company, acquired Metasploit, integrating it into their suite of security tools. Rapid7 has since expanded the framework’s capabilities, incorporating features for intrusion detection, exploit development, fuzz testing, anti-forensics, and evasion techniques.
Who Uses Metasploit?
Metasploit’s extensive functionality and open-source nature make it a valuable asset for a diverse range of users, from DevSecOps professionals to hackers. Its popularity among hackers underscores the importance for security experts to be well-versed in its use, ensuring they can protect systems against the very techniques Metasploit facilitates. The framework supports over 1,677 exploits across 25 platforms, including Android, PHP, Python, Java, and Cisco, and boasts nearly 500 payloads, such as:
- Command Shell Payloads: Enable execution of scripts or commands on the target system.
- Dynamic Payloads: Generate unique payloads to evade antivirus detection.
- Meterpreter Payloads: Allow control over sessions, file transfers, and system monitoring.
- Static Payloads: Facilitate port forwarding and network communication.
Benefits and Applications of Metasploit
To effectively utilize Metasploit, users must gather detailed information about the target system through port scanning, OS fingerprinting, or vulnerability scanning. Once this data is obtained, selecting an appropriate exploit and payload becomes straightforward. An exploit identifies a system weakness, and a payload delivers the necessary code to exploit that vulnerability.
Metasploit comprises various modules and interfaces, including:
- msfconsole: An interactive command-line interface.
- msfcli: Allows command-line access to Metasploit functions.
- Armitage: A graphical Java tool that integrates with Metasploit for visualizing targets and exploits.
- Metasploit Community Web Interface: Supports remote penetration testing.
Ethical and Practical Considerations
While Metasploit is a powerful tool for security professionals, it is also a preferred utility for malicious hackers. Ethical hackers should use measures like VPNs and dedicated VPS to protect their identity and avoid disruptions during testing. Furthermore, Metasploit offers various modules such as exploits, payloads, auxiliary functions, encoders, listeners, shellcode, post-exploitation code, and no-ops (nops).
Getting Started with Metasploit
Metasploit can be downloaded from the Rapid7 website. It requires disabling antivirus software and firewalls during installation and administrative privileges. The framework is pre-bundled with Kali Linux, while Windows users can use an install shield wizard. Initial setup involves creating databases, starting PostgreSQL, and establishing database schemas.
Learning and Using Metasploit
Familiarity with Ruby or other scripting languages like Python can facilitate learning Metasploit. Given the risks involved, it’s advisable to use a dedicated work device for testing. Numerous resources are available to support learning, including Metasploit’s knowledge base and the Varonis Cyber Workshop, which offers tutorials and sessions with industry experts.
By leveraging Metasploit and collaborating with data-driven cybersecurity firms, professionals can enhance their ability to protect networks from exploits and cyberattacks.
How to install Metasploit
You can open your terminal and run the following commands.
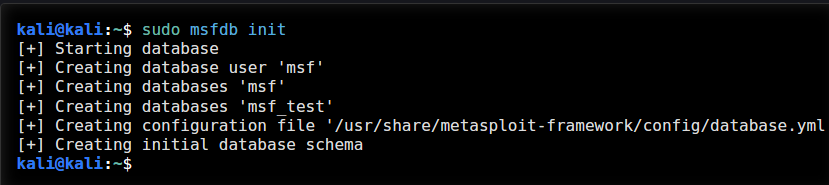
Continuing with MSFDB
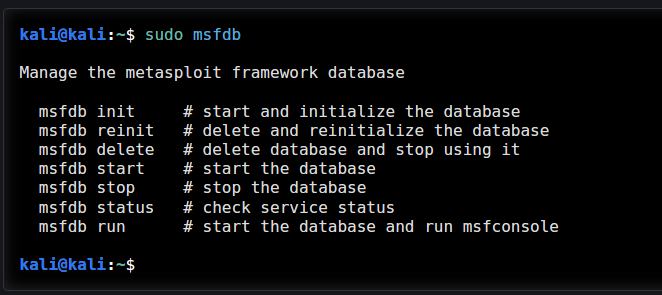
To help interactive with various parts of the Metasploit configuration there is msfdb:
You can run the command sudo msfdb:
Starting the Kali Postgres servive
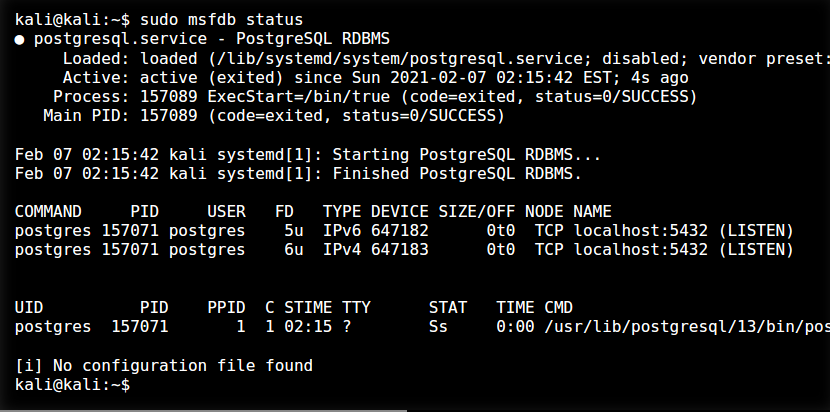
Metasploit uses PostgreSQL as its database so it needs to be launched first:
You can verify that PostgreSQL is running by checking the output of ss -ant and making sure that port 5432 is listening, or using sudo msfdb status:
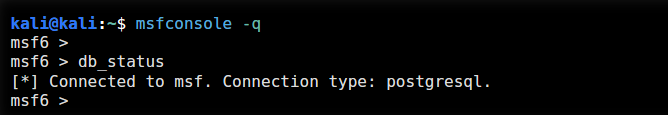
Launch msfconsole in Kali :
Now that the PostgreSQL service is up and running and the database is initialized, you can launch msfconsole and verify database connectivity with the db_status command as shown below:
Last updated 04 Sep 2024, 13:45 +0530 .